Zero Trust Architecture: How to Build an Identity-First Security Model
The rise of hybrid work, cloud adoption, and identity-based attacks has made traditional security perimeters obsolete. This guide explains how Zero Trust and Identity & Access Management (IAM) help organizations secure users, devices, and data with continuous verification and least-privilege access.
Why Zero Trust Is the Future of Cybersecurity
As businesses rapidly adopt cloud services, hybrid work, and mobile devices, traditional perimeter-based security models are no longer enough. Firewalls and VPNs once defined the edge of the network, but today, the most critical security boundary is identity.
This shift has pushed Zero Trust Security and Identity and Access Management (IAM) to the forefront of modern cybersecurity strategies. Instead of trusting users simply because they’re “inside the network,” Zero Trust requires continuous verification, real-time authentication, and strict access controls.
What Is Zero Trust? A Simple Definition
Zero Trust is a cybersecurity framework built on one core principle:
Never trust, always verify.
It assumes every user, device, application, or connection could be compromised, whether they’re inside or outside the network.
This identity-first approach ensures that only verified, authorized, and secure identities can access sensitive data or systems.
Why Identity Is the New Perimeter
Cyber attackers no longer need to “break in.” They just need a password, a stolen session cookie, or a successful phishing attack.
As a result, identity-based attacks have become the top cause of data breaches.
Why identity is now the main target:
Users access apps from anywhere (home, office, public Wi-Fi).
Cloud environments bypass traditional network boundaries.
SaaS apps rely heavily on credentials and tokens.
Attackers use AI-generated phishing to steal login details.
This makes Identity and Access Management (IAM) the frontline defense.
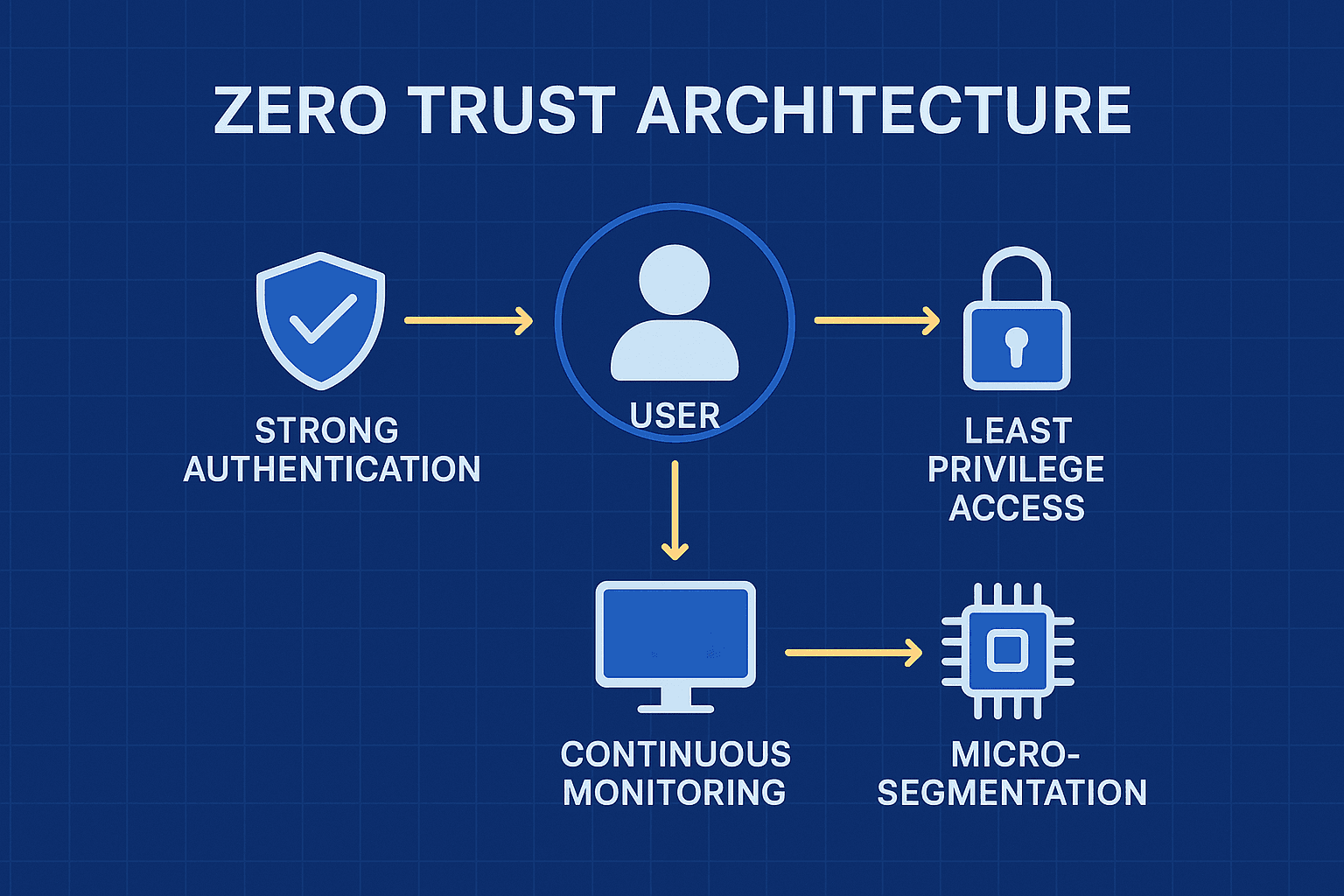
Key Components of a Zero Trust, Identity-First Strategy
1. Strong Authentication & Multi-Factor Authentication (MFA)
Zero Trust demands continuous verification. This includes:
MFA (multi-factor authentication)
Passwordless authentication
Biometrics
Adaptive authentication based on user behavior
These layers make it significantly harder for attackers to use stolen credentials.
2. Least Privilege Access Control
Zero Trust ensures users only receive the minimum permissions required.
Benefits of least privilege:
Reduces insider threat risk
Limits damage if accounts are compromised
Helps comply with security frameworks like NIST and ISO
3. Continuous Monitoring & Risk-Based Access
Instead of granting access once and forgetting about it, Zero Trust monitors:
Login patterns
Device security posture
Location anomalies
Privilege escalations
If something looks suspicious, the system challenges, restricts, or blocks the user automatically.
4. Micro-Segmentation & Network Isolation
By dividing networks into small segments, Zero Trust prevents attackers from moving freely across systems.
This is crucial for:
Cloud networks
Hybrid infrastructure
Highly regulated industries
Benefits of Zero Trust for Modern Businesses
✔ Enhanced Protection Against Data Breaches
Zero Trust reduces the chances of unauthorized access, even if credentials are stolen.
✔ Strong Cloud and SaaS Security
Identity-based controls work seamlessly across multi-cloud environments.
✔ Better User Experience with Passwordless Authentication
Fewer passwords mean happier users and fewer vulnerabilities.
✔ Regulatory Compliance
Zero Trust aligns with GDPR, NIST 800-207, and other global standards.
✔ Protection for Hybrid and Remote Workforces
Location no longer matters, identity does.
How to Start Building a Zero Trust Identity Framework
You don’t need to implement everything at once. Most organizations begin with:
Enforcing MFA and strong authentication
Centralizing IAM and reviewing privilege levels
Securing access to cloud apps and remote devices
Deploying endpoint protection and device posture checks
Adding continuous threat detection and monitoring
Every step strengthens the identity perimeter and reduces risk.
Conclusion: Identity Is the New Cybersecurity Battleground
The cybersecurity perimeter has shifted.
It’s no longer defined by physical networks or office walls; it’s defined by who is accessing what.
This makes Zero Trust, Identity, and Access Management essential components of any modern cybersecurity strategy.
Organizations that adopt Zero Trust early gain stronger protection, better control, and a future-proof security foundation.