Supply Chain, Vendor, Third-Party & Software Risks: The Hidden Cyber Threats Every Organization Must Address
Discover how supply chain attacks, vendor vulnerabilities, and third-party software risks expose organizations to modern cybersecurity threats. Learn key strategies to strengthen supply chain security and reduce third-party risk.
Why Supply Chain Risks Are Becoming a Top Cybersecurity Concern
Today’s businesses run on vast digital ecosystems—cloud providers, SaaS tools, software libraries, external contractors, and global supply chains. This interconnected landscape improves efficiency, but it also opens the door to a potent threat: supply chain and third-party cyber risks.
Attackers have learned that the easiest way into a large organization is often through a smaller, less-protected vendor. This shift has made supply chain attacks one of the fastest-growing cybersecurity threats across every industry.
To stay secure, companies must rethink how they assess vendor relationships, software dependencies, and third-party integrations.
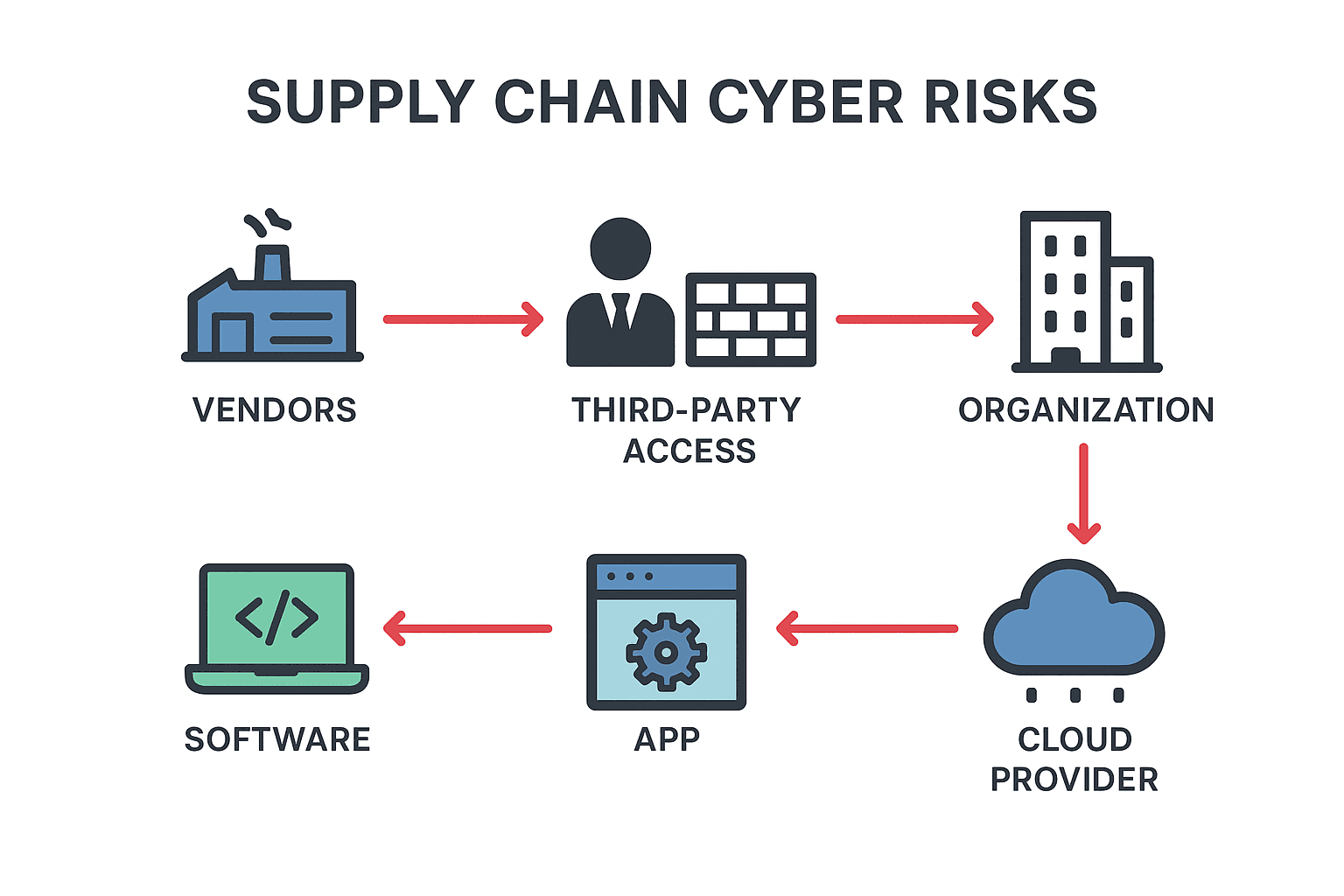
What Are Supply Chain and Third-Party Cyber Risks?
Supply chain cyber risks occur when attackers exploit vulnerabilities in the systems, services, or software of external partners to gain access to an organization's data or networks.
These can include:
Vendors and service providers
Contract manufacturers
External developers
Cloud and hosting partners
Software suppliers and open-source libraries
Hardware manufacturers
In a digital-first world, third-party risk is no longer optional; it’s unavoidable.
Why Supply Chain Attacks Are Rising So Quickly
1. Vendors Have Trusted Access
Many vendors are granted high levels of access for convenience—remote maintenance, integrated APIs, cloud authentication, etc.
Attackers exploit this trust to bypass direct security barriers.
2. Smaller Vendors Often Have Weaker Cybersecurity
Hackers frequently target the "low-hanging fruit": small or mid-sized suppliers with outdated security practices.
3. Software Has Become Incredibly Complex
Modern applications rely on thousands of components, especially open-source dependencies.
One compromised library can infect millions of users before detection.
4. Limited Visibility Into Vendor Networks
Most organizations can’t see what security controls their partners use, making it difficult to identify risks before they become breaches.
Types of Supply Chain, Vendor & Software Risks
1. Third-Party Vendor Risks
These occur when external partners have access to internal systems.
Examples:
Managed IT service providers
Payment processors
HR and payroll vendors
Marketing agencies with shared platforms
2. Software Supply Chain Risks
Some of the most damaging attacks come from compromised software updates or malicious code inserts.
Risks include:
Vulnerable software components
Corrupted CI/CD pipelines
Unverified or unsigned updates
Malicious dependencies in open-source libraries
3. Hardware & Firmware Risks
Before equipment even reaches your organization, it could already be compromised.
Examples:
Tampered firmware
Counterfeit devices
Backdoored hardware components
4. Operational Supply Chain Disruptions
Even non-digital vendors can cause cybersecurity pain, especially if they’re hit by ransomware.
Supply chain downtime = business downtime.
Real-World Impact of a Supply Chain Attack
A single compromised vendor can lead to:
Sensitive data exposure
Ransomware spreading across connected networks
Business interruption and supply chain delays
Compliance violations and financial penalties
Reputation damage and customer loss
Intellectual property theft
Loss of operational continuity
In severe cases, organizations may face months of recovery—even though the initial breach didn’t start with them.
How to Reduce Supply Chain and Third-Party Cyber Risks
1. Implement a Third-Party Risk Management (TPRM) Program
Build a formal process for evaluating vendor security:
Security questionnaires
Risk scoring
Cyber insurance verification
Compliance checks (ISO 27001, SOC 2, etc.)
Annual vendor audits
Make cybersecurity part of vendor selection—not a checkbox.
2. Apply Zero Trust Principles to Vendor Access
Never assume vendors or integrations are safe.
Use:
Least privilege access
Time-restricted permissions
MFA on all vendor accounts
Network segmentation
Conditional access policies
Vendors should never have more access than necessary.
3. Strengthen Software Supply Chain Security
Integrate security into every stage of development:
Scan code dependencies continuously
Use signed software packages
Secure CI/CD pipelines
Monitor for vulnerability disclosures
Adopt DevSecOps practices
This reduces risk from open-source or third-party libraries.
4. Increase Monitoring and Visibility
Use advanced tools to detect suspicious behavior:
API monitoring
Endpoint detection and response (EDR)
Behavior analytics
Log management
Real-time alerts
Visibility is the most vigorous. defense against hidden threats.
5. Establish Vendor Incident Response Requirements
Require vendors to:
Notify your organization promptly after a breach
Share logs and incident details
Cooperate during investigations
Follow your security policies when accessing internal systems
A vendor mistake should never become your disaster.
Why Supply Chain Security Is Now a Business Necessity
Every organization depends on dozens, or sometimes hundreds, .of interconnected partners.
Each link added to the chain introduces new vulnerabilities. Even if your cybersecurity is strong, it only takes one weak vendor to jeopardize the entire system.
Cybersecurity today isn’t just about protecting your business.
It’s about protecting the ecosystem your business depends on.
Conclusion: Strengthening the Digital Supply Chain
Supply chain, vendor, and software risks aren’t new—but their scale and impact have grown dramatically.
Organizations must shift from reactive security to proactive, continuous evaluation of every third-party relationship.
By improving visibility, enforcing Zero Trust policies, and implementing strong vendor risk management, businesses can significantly reduce the chances of a supply chain breach—and build a more resilient future.